I don’t envy our clients. As a digital professional whose head is constantly swimming in a flood of new technology, I can only imagine what it must be like for a non-digital professional to manage the technical challenges their company website brings. And, unfortunately, as I’ve written in the past, the consequences of not learning about and acknowledging the few technical considerations that relate to website management, can lead to catastrophe.
One of the most severe consequences we’ve witnessed (as we wrote about here) is the company’s site falling prey to a security breach of one of many different types. Of all the types we’ve witnessed, over the years, one type sticks out as both the most common and the most preventable. It’s called the Brute Force Attack.
What is a Brute Force Attack?
A brute force attack, simply stated, is an attack which bombards the WordPress login panel with an onslaught of login attempts, all of which attempt to guess that site’s username and password combination. It capitalizes on the weakest link in any security loop: human error and naivete. Such an attack exploits two mistakes a novice site owner is inclined to make, namely, not changing the WordPress username from the default ‘admin’ name and, secondly, choosing an easily guessed password.
How Common are Brute Force Attacks?
In our anecdotal experience, exceedingly common. In fact, every site we monitor currently has experienced scores of unauthorized login attempts. But don’t just take our word for it. In this chart, our security plugin vendor, Sucuri, tracks the incidence of Brute Force attacks on the sites their monitoring software is installed on. As one can see, it shows a steady rise in such attacks, rising steadily until September of 2015.
How to Avoid Brute Force Attacks
Not falling prey to a brute force attack devolves to a very simple strategy. Don’t use an easy-to-guess WordPress login name and don’t use an easy-to-guess password. Take a look at this screenshot, which represents a very typical client’s log of unauthorized login attempts. 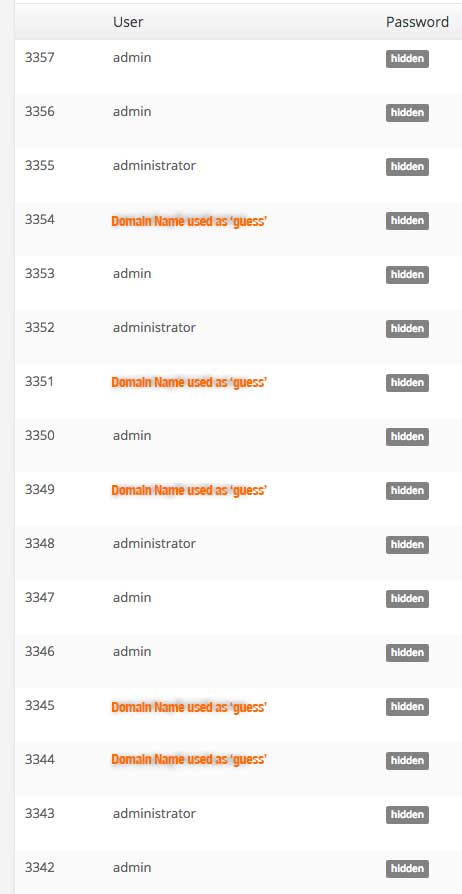 The clear conclusion we can draw from it is that attackers look for low-hanging fruit, in the form of typically used usernames. These three are almost always:
The clear conclusion we can draw from it is that attackers look for low-hanging fruit, in the form of typically used usernames. These three are almost always:
- Admin. The default WordPress username. The one it ships with. The one you need to immediately change. (The best way to do this, by the way, is to simply make a new security-minded username, with full administrative privileges, and delete the default ‘admin’ username, assigning any post content to the new user. Using this method completely removes another frequent doorway to exploitation, namely it eliminate the default ID of ‘1’ assigned to the ‘admin’ user.) by logging into the Users panel in WordPress, creating
- Administrator/administrator. A very simple (and sometimes accurate) guess on the part of the hacker that, if you’re not going to use the default ‘admin,’ an obvious alternate name might be ‘administrator.’
- The domain name of the site, i.e., ‘splatworld.’ A very common name for the inexperienced WordPress owner to assign as their login name is the URL of the site’s home page. While logical from the owner’s point of view, it’s also so common that it is the third most ‘guessed’ username used among Brute Force attackers.
Once an attacker has guessed your username, he’s halfway there. All that stands between him and the utter destruction he can then wreak is your username’s password. That’s why you need a strong one. I know from professional experience that many clients are loathe to use a secure password generator to create a secure, but unmemorizeable password but, my advice is, “get over it.” My current password file is about ten pages worth of data; I no more can recall most of my passwords than I can the number of years I’ve spent on this earth. (Okay, it takes a little bit of forced lack-of-recall to forget that, but I try everyday!) They days of choosing ‘1234’ or your third child’s name as a password are long gone. Just commit to upper and lowercase letters, lots of numbers and a few special characters and get over it.
The good news is that, outside of the very simple strategy I’ve just outlined, there’s nothing else a site owner really needs to do to bring the likelihood of a successful brute force attack down to a near zero percent chance. In past and future posts we did/can talk about other methods of ‘hardening’ the security of your site, but, just following the above advice will go a long way towards making your site more secure.